[ad_1]
Amazon will be hosting its Prime Day sale in India on July 23 and July 24 but ahead of the online shopping extravaganza, Check Point Research (CPR) has detected a sharp increase in daily Amazon-related phishing attacks as cybercriminals try to exploit shoppers on the lookout for a good deal.
During the first week of July, CPR detected a 37 per cent increase in such phishing attacks compared to the daily average in June. It also found 1,900 newly registered domains with the word “amazon” in them; 9.5 per cent of these were found to be either suspicious or malicious. In the week prior to Prime Day 2021, CPR had discovered 2,303 new such domains with 38 per cent of them found to be risky.
CPR also came across many phishing emails that were disguised to look like emails from Amazon to lure unsuspecting users into clicking on malicious links or divulging personal information that can then be used in other attacks.
One example is the email below, which looks like it is informing the user of a cancelled order due to payment issues. But in actuality, it contained an ISO file attachment that would have left an executable dropper malware in the user’s computer if they opened it.
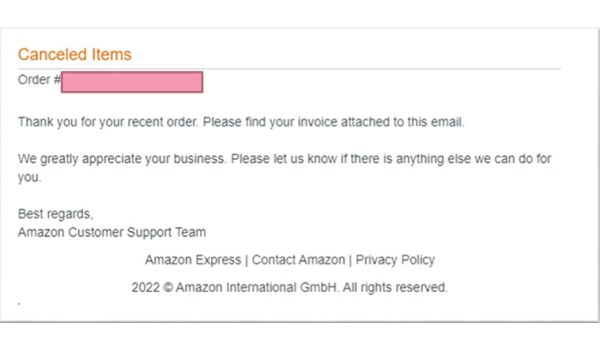 Image credit: Check Point Research
Image credit: Check Point Research
How to recognise phishing emails
Attackers use many different techniques to make malicious emails look legitimate and if you are aware of some of them, it would be easier for you to spot and avoid phishing attacks. Here are some of the most commonly used phishing attack techniques, as identified by CPR.
Fake domains
Using a fake lookalike domain that appears to be from a legitimate company is one of the most common email phishing techniques. For example, instead of the email address help@company.com, attackers could use help@cornpany.com, which might fool users if they don’t pay much attention. Similarly, attackers could use help@company-support.com.Even thought this may seem legitimate at first glance, the domain wouldn’t necessarily be owned by or associated with the company in question.
Incorrect grammar or spelling mistakes
Phishing emails often contain grammatical errors and mistakes because they are sometimes written by people who are not fluent in the language. Sometimes, they do this because they only want people who would fall for the scam to respond. Either way, emails from legitimate organisations are unlikely to contain such errors and that is one easy way to spot phishing mails.
Risky attachments
Many phishing attacks rely on tricking users into downloading and running malware attached to the mail. In order to do this, phishing emails often contain suspicious attachments. For example, an email that is supposed to deliver an invoice may contain a .zip file.
Psychological tricks
Phishing emails often employe psychological tricks to convince users into doing something against their interest like installing malware or sharing sensitive information. One such method is where they create a false sense of urgency by telling the recipient that something needs to be done right away. If a recipient falls for this, they might be in too much of a hurry to notice that they are being scammed.
Another trick employed by scammers is when they pretend that the email is coming from an authority figure, like the CEO of a company or a manager. This takes advantage of the fact that the recipient might be inclined to follow orders from their bosses at work. Yet another technique involves threatening the recipient with consequence if they do not do what the attacker says, like revealing sensitive information about them. They do this to make the recipient act in a certain way due to the fear of embarrassment or punishment
What to do if you identify a phishing email
If you identify an email as a phishing scam, do not click on links, open attachments or reply to the email. After that, report them to the IT or security team at your organisation so that they are appraised of the risk. At this point, it would be best to delete the email so that you reduce the chance of accidentally clicking on it at a later date.
!function(f,b,e,v,n,t,s)
{if(f.fbq)return;n=f.fbq=function(){n.callMethod?
n.callMethod.apply(n,arguments):n.queue.push(arguments)};
if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version=’2.0′;
n.queue=[];t=b.createElement(e);t.async=!0;
t.src=v;s=b.getElementsByTagName(e)[0];
s.parentNode.insertBefore(t,s)}(window, document,’script’,
‘https://connect.facebook.net/en_US/fbevents.js’);
fbq(‘init’, ‘444470064056909’);
fbq(‘track’, ‘PageView’);
[ad_2]
Source link


